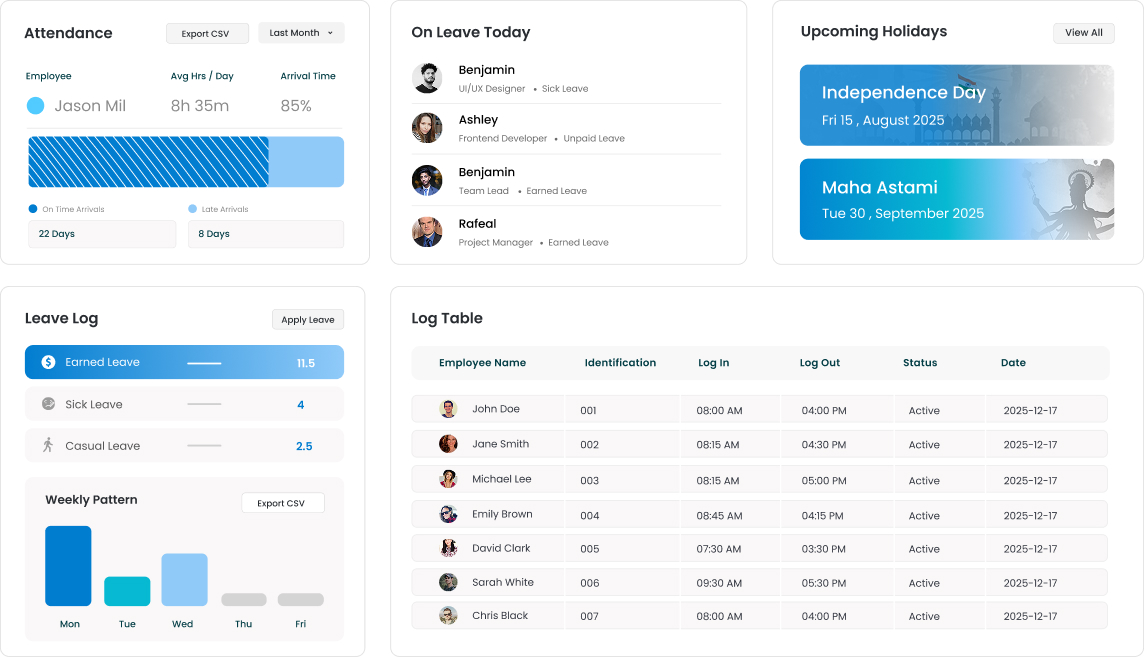
Enhance Security with an Advanced Access Control System
Improve workplace security with the help of advanced access control system that easily integrates with visitor management. Make sure only authorized persons are allowed entry, optimize check-ins and monitor access in real-time for a safe and more efficient environment.
Why are Businesses Upgrading to Modern Access Control Systems?
Traditional visitor management systems depend on paper logs, other manual processes and outdated methods of security. Thus, leaving the businesses more vulnerable. Use of modern access control systems improve security, efficiency and provide easy integration.
Lack of Real-time Monitoring
Traditional systems offer immediate insights into visitor management, increasing the risk of security. A modern access control system allowing real-time alerts and tracking to prevent unauthorized access.
Inefficient Manual Check-Ins
Paper-based visitor logs cause unnecessary delays in the entry processes and lead to errors. Digital visitor access management digitizes the check-ins, allowing a fast, hassle-free experience for guests and employees.
No Integration with Security Systems
Standalone visitor management systems lack integration with emergency response systems. An efficient and advanced access control system easily connects with security infrastructure to improve threat detection and response.
Increased Risk of Unauthorized Entry
Traditional visitor badges and sign-in sheets can be missused. Modern systems make use of biometric authentication, smart ID cards and AI-driven verification to ensure only authorized individuals get access.
Compliance and Audit Challenges
Outdated or traditional systems make it difficult to maintain safety regulations and compliance. Automated access control solutions offer automated reports and audit logs for regulatory compliance and data security.
Limited Visitor Access Control
Traditional visitor management provides no flexibility in defining the access levels of visitors. An automated access control system assigns permissions, restricting movement based on schedules, roles or departments.
Surprising Facts About Access Control & Visitor Management
Did you know that traditional access control systems are not designed to manage temporary credentials effectively? Businesses often struggle with security gaps, manual processes, and inefficiencies when handling visitor access. Here are some eye-opening statistics:
12 Minutes is the average time it takes to issue credentials, causing unnecessary delays and administrative burdens.
A modern visitor access management system streamlines credential issuance, reduces costs, and enhances security by integrating with advanced access control solutions. Isn’t it time to upgrade your security?
Top Challenges in Visitor Access
Management
Managing visitor access effectively is crucial for security, compliance, and operational efficiency. However, many organizations face challenges in controlling and monitoring visitor movements. Here are the top issues businesses encounter:
Unauthorized Access Risks
Without a robust access control system, unauthorized individuals can enter restricted areas, leading to potential security threats, data breaches, and safety concerns for employees, assets
Manual Check-In Inefficiencies
Traditional paper-based visitor logs or outdated manual check-ins slow down operations, increase human errors, and make it difficult to track visitor history for audits or security reviews.
Lack of Real Time Monitoring
Organizations struggle with monitoring visitor movements in real time, making it harder to detect unauthorized access, enforce security policies, or respond to emergencies effectively.
Compliance and Regulatory Challenges
Many industries require strict compliance with visitor access management policies. Failure to maintain accurate visitor records can lead to legal penalties, data protection violations, and reputational damage.
Limited Access Control Customization
Many businesses lack the ability to assign different access privileges to visitors based on their purpose, duration of stay, or location, increasing security vulnerabilities within their premises.
Ineffective Badge or Credential Management
Issuing and revoking visitor access badges manually can be slow and error-prone, increasing the risk of unauthorized badge use and security loopholes.
Security Threats from Unverified Visitors
Without proper screening procedures, businesses risk allowing potential threats into their premises, such as individuals with criminal intent or those who fail to meet security clearance requirements.
Integration Issues with Existing Systems
Many companies face difficulties integrating visitor management solutions with existing security infrastructure, leading to fragmented data, inefficiencies, and a lack of centralized control over visitor access.
Key Benefits of Implementing a Smart Visitor Access Management Solution
A smart visitor access management system enhances security, streamlines operations, and ensures compliance with regulatory requirements. Here are the key benefits of integrating an advanced access control solution into your organization:

A smart visitor management system prevents unauthorized access by verifying identities, issuing temporary credentials, and tracking movements in real time, reducing security risks and ensuring only authorized visitors can enter restricted areas.

Automated check-in processes, digital badges, and self-service kiosks provide a seamless visitor experience, reducing wait times, eliminating paperwork, and offering a professional first impression for guests and business partners.

Organizations can track visitor movements in real time, receive alerts for security breaches, and generate detailed reports for audits, helping to maintain compliance with industry regulations and internal security policies.

Businesses can assign different access levels based on visitor roles, ensuring that guests, contractors, and employees only enter authorized zones, improving security while maintaining operational efficiency.

With automated badge activation and deactivation, organizations can eliminate unauthorized badge usage, ensuring that visitors’ access permissions expire automatically upon exit or after a predefined time limit.

Modern visitor access management solutions integrate with security systems, access control software, and compliance platforms, providing centralized control, reducing administrative workload, and enhancing overall security infrastructure.
Effortless Visitor Access Management for Secure Workplaces
Handling visitor access is crucial but is often an overlooked aspect of security. Convex vZit provides complete control and real-time visibility into the movement of visitors, ensuring easy and secure access management for all visitor types.

Issue Temporary Access Credentials
Offer day passes for visitors, temporary workers or contractors or temporary workers with automatic expiration upon sign-out. Prevent unauthorized re-entry by enforcing one-time-use credentials, ensuring tighter security and controlled visitor management.

Provide Emergency or On-Demand Credentials
Allow immediate access to visitors who need urgent or one-time entry. Generate QR code-based credentials that allow easy sign-in without disturbing continuous security protocols or processes of visitor management.

Allow Recurring Access for Regular Visitors
Grant scheduled access to employees, vendors or maintenance personnel requiring frequent entry. You can set validity periods for access credentials, automatically renewing or expiring based on predefined routines to optimize security management.

Assign Event-Specific Credentials
Issue visitor credentials for special events like conferences, meetings and other corporate events. The access remains active only for the duration of the event. This ensures seamless entry and automatic expiration as the event concludes, decreasing unauthorized risk of access.
Must-Have Features in a Smart Visitor
Access Management System
A strong visitor access management system ensures efficiency, security, and easy visitor movement. With special features such as AI-driven access, cloud management and automated credential control, businesses can improve security while simplifying visitor operations.
Issue Access Control
Card on Sign In
Automatically generate and assign access control cards upon visitor sign-in. Ensure authorized entry and restrict movement of visitors to designated areas, decreasing security risks and enhancing visitor management efficiency.
Cloud Based
Management
Monitor and control the access of visitors from anywhere with the help of a cloud-based system. Allow real-time updates, remote credential management and easy integration with the current security infrastructure for improved control.
Assign Different Access
Privileges to Visitors
Grant customized access levels depending on the type of visitors, role and purpose. Limit access to sensitive areas and ensure compliance with security protocols without disturbing operational efficiency.
Allocate Visitor Types
for Specific Locations
Define categories of visitors as well as assign access based on designated locations. This helps in preventing authorized entry and improves security monitoring.
Universal
Controller
Integrate and handle several access points from a single interface. A universal controller optimizes visitor authentication, making security operations more effective and scalable.
Artificial
Intelligence
Utilize AI-powered analytics to detect unusual visitor behavior, automate decision-making and predict security threats.AI-driven insights help enterprises proactively improve security measures
Automatic Visitor Access
Card Deactivation
Make sure visitor access credentials expire automatically at the end of a specific period or upon sign-out. This helps in preventing unauthorized re-entry and strengthens complete security.
Future-Proof Your Security with Our Access Control System
Enhancing Visitor Entry and Management Efficiency
Advantages
- Swift egress relieves traffic pressures
- Adds effective maintenance and management
- Offers visual verification of alarm events
Features
- Multiple authentication credentials: Face, fingerprints, ID cards, PIN codes, etc.
- Visual monitoring, reflecting access control status.
- Real-time alarms, abundant alarm-linkage apps.
- Intercom for request entry at the door
Stay safe with high protection levels
Advantages
- Effectively enhances the security levels for accessing specific areas
- Abundant linkage for alarms and events
- UPS enhances system stability
Features
- High security access control apps available, like anti-pass back, interlock, multiple authentications, etc.
- Support UPS
- Access control alarm with several linkages
Protection during emergencies
Advantages
- Decreases the risks for people in emergency areas
- Enhances the efficiency of evacuation
- Informs employees of emergencies in timely manner
- Empowers speedy and accurate measures as per the requirement
Features
- Emergency mode can either be launched manually or by linking to system
- Doors are automatically kept open and IP speakers broadcast message repeatedly
- Send emails, app notifications or SMS messages automatically to all the employees
- Real-time people counting in emergency areas
Get a Custom Access Control Solution for Your Business
What Sets Our Access Control System Apart?
Our specialized access control systems ensure premier security, easy integration and effective visitor management. With the help of cutting-edge technology and smart automation, we offer reliable, future-read and scalable solutions for modern businesses.
Advanced Security & Threat Detection
Our system makes use of AI-driven analytics and real-time monitoring for detecting security threats, ensuring effective risk management and safeguarding your facility against unauthorized access.
Seamless Integration with Existing Systems
Easily integrate your current security infrastructure, including CCTV, visitor management platforms and alarms, ensuring an efficient and unified security ecosystem.
Scalable & Customizable Solutions
No matter whether for small offices or for big enterprises, our visitor access management system scales effortlessly, providing customized access control configurations for meeting the unique needs of businesses.
Cloud-Based Remote
Management
Monitor and control access remotely with the help of a cloud-based platform, enabling real-time credential updates, system handling and visitor management from anywhere.
Automated &
Contactless Access
Allow touchless authentication with biometric recognition, smart access cards and mobile credentials, improving the visitor experience.
Compliance &
Data Protection
Ensure regulatory compliance with advanced encryption and access logs, keeping sensitive information secure and maintaining industry-standard for safety protocols.
What Our Client's Say About Us
Seamless Visitor Experience
I’m genuinely impressed with how user-friendly the Convex vZit application is! The setup was smooth, and ever since we installed it, the security at our premises has noticeably improved. Visitors can check in quickly, and we no longer have long queues at the entrance — it’s made entry so much faster and hassle-free. Highly recommended for anyone looking to modernize their visitor management!
AI-Powered Check-In
What I love most about Convex vZit is the seamless pre-registration feature and the advanced AI face recognition. Guests can pre-register before they even arrive, and when they show up, the AI facial recognition makes entry effortless and secure — no need to fumble for ID cards or explain who they are. It’s a game-changer for ensuring only authorized visitors get in, and it saves so much time for both guests and staff!
Smart Multi-Tenant Solution
As a company operating across multiple offices, the multi-tenancy model of Convex vZit has been a lifesaver. We can manage visitor flows at all our locations from one dashboard, with separate settings and workflows for each site. It’s scalable, efficient, and keeps our visitor data secure and isolated per tenant — exactly what we needed to handle the complexity of a multi-location business.
Frequently Asked Questions
What is Visitor Management System?
A visitor management system is a cloud-based system which allows business organizations to welcome track and manage guests aur visitors in a facility, building, business place or other locations.
Policies or strategies of visit a management can vary depending on the organization, facility type, geographic location or industry.
Can the system be integrated with the existing security infrastructure?
Yes, our system easily integrates with alarms, identity verification, CCTV cameras and other security systems. This ensures an efficient and unified security ecosystem.
How does an access control system improve security for businesses?
It helps in preventing unauthorized entry by providing access only to the verified visitors, employees and contractors. Features such as AI monitoring, real-time alerts and automatic credential deactivation further strengthen security measures.
Is the system cloud-based and can I manage access remotely?
Yes, our cloud-based solution provides you to handle visitor access, update credentials in real-time, monitoring security events using a centralized dashboard from anywhere.